DNS Hijacking, also termed DNS Redirecting or DNS Poisoning, is a stratagem cyber pillagers use. They trample upon a computer’s IP settings on the Internet to block access, restrict, and censor content.
By overriding a computer’s IP settings, the hijacker directs it to a rogue DNS server instead of the user-friendly domain names. This can also be achieved by monitoring and probing directly into the traffic at imperative routing spots.
The Great Firewall of China, which the government uses to achieve Internet censorship in China, is the biggest example of DNS hijacking.
What is DNS
Domain Name Service is abbreviated as DNS. It is an Internet service that translates URLs such as Google.com to an IP address 8.8.8.8. Every website has an IP address linked to its URL via DNS. The DNS server holds a record of the IP address of every website along with the corresponding URL. Here, the URL depicts the name and the IP address, just like a phone book holding records of the enlisted people with their addresses.
Many companies publish the website’s DNS address and an algorithm that keeps them updated simultaneously.
The DNS system is functioned by your ISP (Internet Service Provider) and many other private business organizations. Your computer is configured to use the ISP’s DNS server. But these settings can be changed manually.
DNS Hijacking – Mechanism
When you enter a URL into your browser’s address bar, it is sent to a DNS server to resolve into an IP address, mapping you to your friendly domain names. However, a wrong DNS server is often reached due to inadequate checks and balances.
An attacker might hijack the DNS, functioning between the computer and the DNS server, from a rogue device. If that’s the case, the hacker now owns the DNS server, as he might have changed the DNS settings and gained access to your computer.
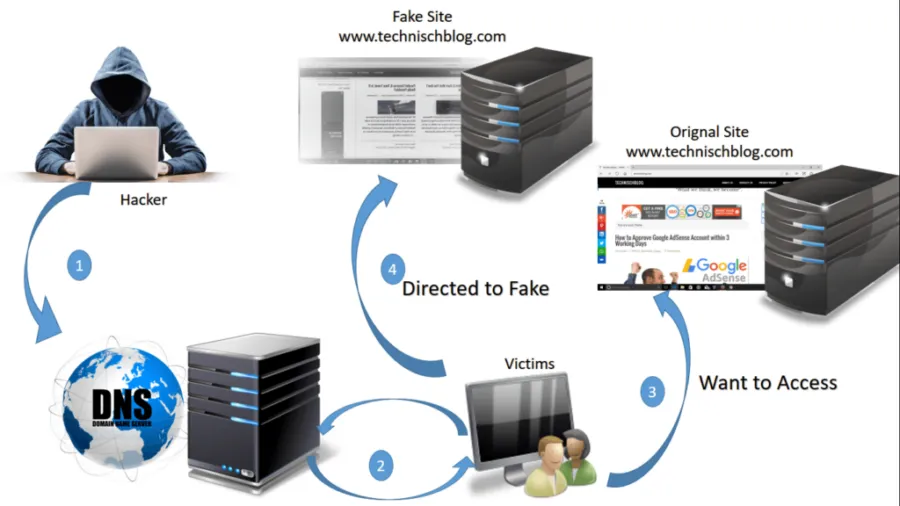
Now comes the point where the DNS server contaminates its records by swapping the IP addresses of the sites you wish to visit with those of another site that might be already infected with malware.
If an experienced hijacker carries out DNS hijacking, he might masquerade websites. As a result, he may compile sensitive information of users as well as the passwords and IP addresses of many websites.
In many cases, DNS hijacking is also carried out by using sophisticated malware such as a trojan horse. The DNSChanger trojan is a form of malware that profited about 14 million USD by hijacking the DNS settings of over 4 million computers through deceptive advertising revenue.
DNS Hijacking – Censoring the Internet
Internet censorship is enforced by many countries that require Internet Service Providers to cut off some specific domains from their DNS servers. However, this is a comparably easy form of hoodwinked censorship.
On the other hand, when a hijacker operates the whole network, he can restrict and block contractual DNS servers entirely or apply Deep Packet Inspection to block or misdirect requests specifically.
DNS Hijacking – Prevention
After going through the dangers you are exposed to with DNS hijacking, we will share the easiest way to prevent DNS hijacking.
Domain Name System Security Extensions, abbreviated as DNSSEC, can be considered a DNS hijacking analysis used to verify the integrity of the DNS server and for protection purposes. DNNSEC minimizes the chances of a hijacker masquerading as a DNS, but it is a tough job for a user to set up, validate and monitor, unlike HTTPS in web servers.
A good antivirus program can protect your computer against such attacks, but keeping it updated is essential.
DNS Hijacking – Fix
Strong privacy concerns are related to opting for the correct DNS server, as they will see each domain you try to connect to. You can change the DNS server to avoid censorship by your local Internet Service Provider. But eventually, this power will be withdrawn from the hands of your Internet Service Provider for a substantial cause.
You may change your DNS server to an autonomous DNS service like OpenDNS or Google DNS.
Different VPNs run their DNS servers, and if you connect to one of the VPNs, you can automatically use their servers. No one will be able to hijack your connection, and thus, your information will be well-protected. Such VPNs ensure that the sites you wish to visit resolve correctly and are not censored by the ISP or government.
Conclusion
DNS hijacking has been observed to be causing a menace in the Internet world. Not a single organization can be seen as well-protected against DNS attacks. An example of DNS hijacking is the hackers’ group known as the Iranian Cyber army that took Twitter by storm.
DNS is essential in resolving the URLs you enter into your browser’s address bar. It is a sort of recurrent operation that aids your browser in getting the IP address of the website you wish to reach. The delay the browser takes while attempting to resolve the IP address is used as an advantage by the hijacker. This results in DNS hijacking. The dangers of DNS hijacking may include the attacks of pharming and phishing.
To avoid DNS hijacking, you can use good security software, or you may change your DNS server. Following such basic steps, you can thoroughly protect yourself from DNS hijacking and surf the web without restriction or censorship!
Share this article
About the Author
Rebecca James is an IT consultant with forward thinking approach toward developing IT infrastructures of SMEs. She writes to engage with individuals and raise awareness of digital security, privacy, and better IT infrastructure.
More from Rebecca JamesRelated Posts

What Is VPN Split Tunneling And How Does It Work? Which VPN Offers?
Split tunneling is a VPN feature that allows you to route some of your traffic through the VPN tunne...

What Is VPN Encryption, Types, Protocols And Algorithms Explained
Encryption is a method used to enhance the security and privacy of the data or information that is s...

Why is Opera VPN Not Working? How To Fix Opera VPN?
Author findings: Overall, it’s a slower VPN to use. Also, it will provide just a proxy tu...

How does a Firewall, Anti-Virus and, VPN Differs? Explained!
More often than not, most people tend to forego their devices’ security for pure confusion. Wi...

A Guide to Choosing the Right VPN for Downloading
How to hide downloading files from ISP? From the very start of the hilarious popularity of P2P file-...
What is Port Forwarding and how does it work?
Port Forwarding is a technique used to redirect computer signals between the local network and the i...





