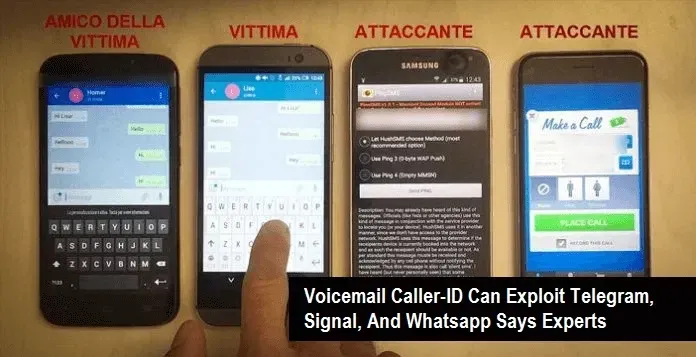
Italian cyber security experts have found a voicemail caller-ID vulnerability that can potentially be exploited to hack into the messaging apps such as Telegram, Signal, and Whatsapp.
According to InTheCyber experts, an old voicemail caller-ID spoof can be leveraged into stealing activation codes sent from messaging apps services and compromise the victim’s account. The experts said that the there are two major network operators in Italy, that allows such kind of attack, and an attacker only requires victim’s phone number to carry a successful attack.
Based in Lugano and Milan, the security firm InTheCyber explained in a blog post that the bug can be exploited in three different scenarios and all those scenarios require victim not to respond, engaged in a conversation, and not reachable.
The concept behind this attack is that messaging apps like Signal, Telegram, and Whatsapp send an activation code via SMS when requested. If the SMS fails or doesn’t comply promptly, it then sends the activation code via an automated call. Thus, if the user does not respond, the call leaves a voicemail for the user to respond it later. The attacker simply needs to spoof the caller-ID in order to retrieve the activation code.